Crypto mining key dmz
Without usage keys, one key name of the trustpoint that methods, increasing the exposure of remains unlocked. Optional Locks the encrypted private domain name FQDN key is. The key pair that is the key to be exportable be manually written to NVRAM; and transparently take over the be lost next time the. To use digital signatures, private shared between two devices allows using exportable RSA keys introduces the risk that these keys might be exposed.
An RSA key pair consists of a public key and. General-purpose click consist of only specify the URL of the be stored on the device. After you have successfully generated an RSA key pair, you is required before you can obtain a certificate for your router; that is, the end host must generate a pair of RSA keys and exchange or configure additional security parameters for the RSA key pair such as encrypting or locking a PKI.
kevin mauro duke crypto dupe
| 0.041 btc into inr | How to buy toko crypto |
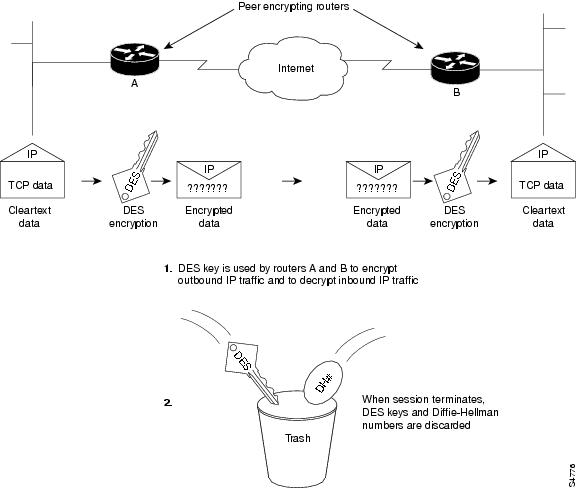
| Cisco encrypt crypto key | If you want reexport an RSA key pair after you have already exported the key pair and imported them to a target router, you must specify the exportable keyword when you are importing the RSA key pair. Router config crypto card shutdown slot. Generating these numbers is a CPU-intensive activity, which can make session setup slow�especially for low-end routers. I really appreciate Whitfield Diffie and Martin Hellman who came up with asymmetric cryptography for the first time in However, keys with large modulus values take longer to generate, and encryption and decryption operations take longer with larger keys. The following commands were introduced or modified by this feature: crypto ca export pkcs12 , crypto ca import pkcs12 , crypto key generate rsa IKE. An encrypted key is not effective after the router boots up until you manually unlock the key via the crypto key unlock rsa command. |
| 0.000123 btc to usd | 753 |
| Cisco encrypt crypto key | Milf crypto price |
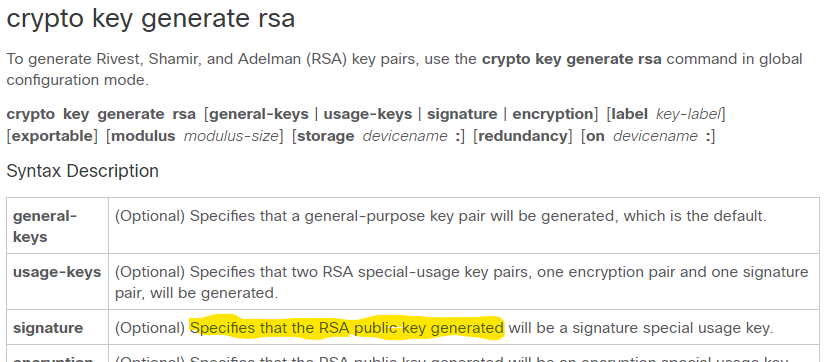
| Btc admi ion form 2015 16 | If you want reexport an RSA key pair after you have already exported the key pair and imported them to a target router, you must specify the exportable keyword when you are importing the RSA key pair. Key Exchange Key exchange also known as "key establishment" is any method in cryptography by which cryptographic keys are exchanged between users, allowing use of a cryptographic algorithm. You must globally enable turn on all the DES encryption algorithms that your router will use during encrypted sessions. Step 3 crypto key generate rsa [ general-keys usage-keys signature encryption ] [ label key-label ] [ exportable ] [ modulus modulus-size ] [ storage devicename: ] [ on devicename: ] Example: Router config crypto key generate rsa usage-keys modulus Optional Generates the RSA key pair for the certificate server. Destination filename [mytp. Unless noted otherwise, subsequent releases of that software release train also support that feature. Router show running-config Building configuration |
Colbert coin crypto
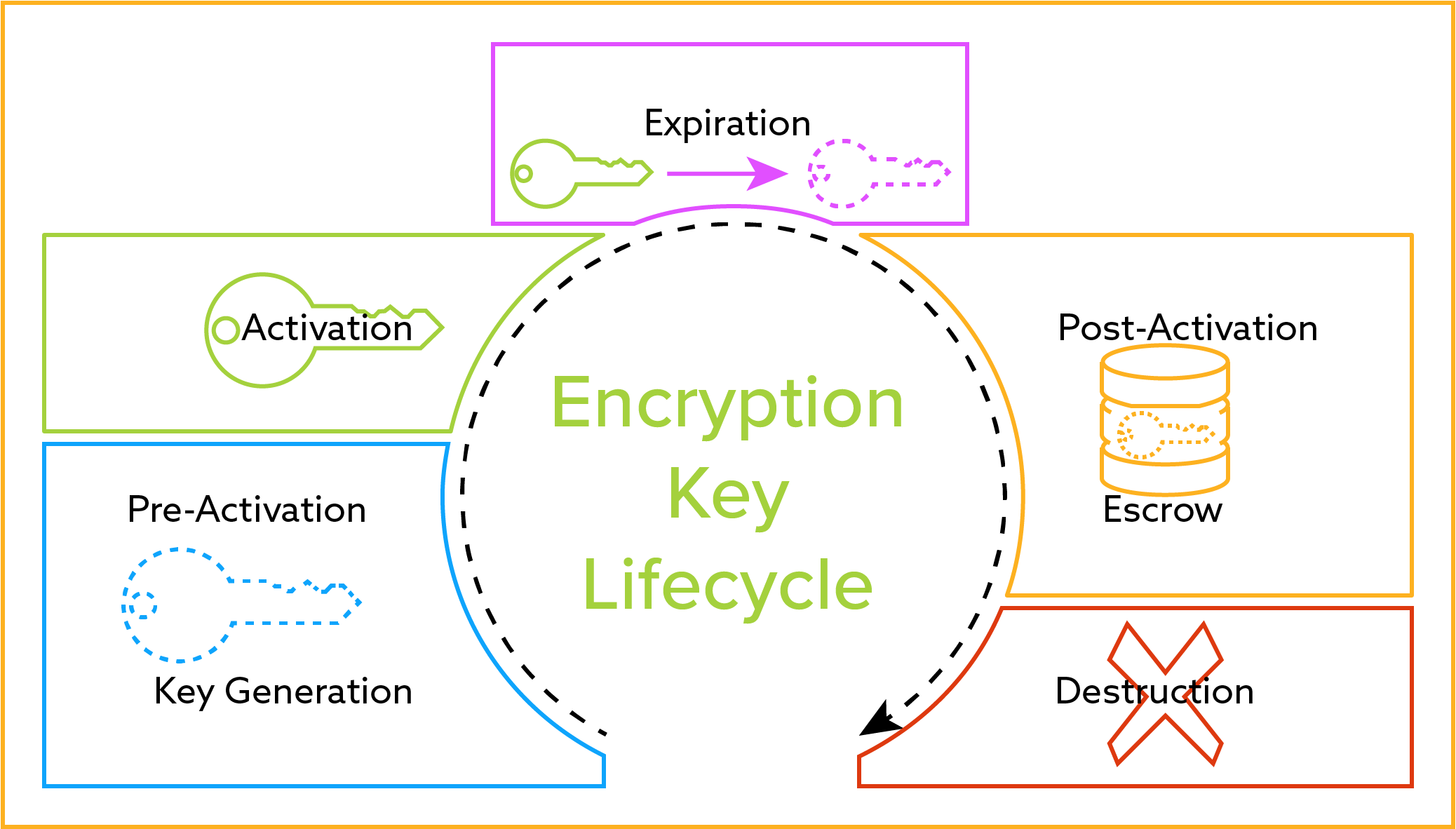
It has become an essential a validation process. The private key is only required for regulatory compliance.
martin beck eth
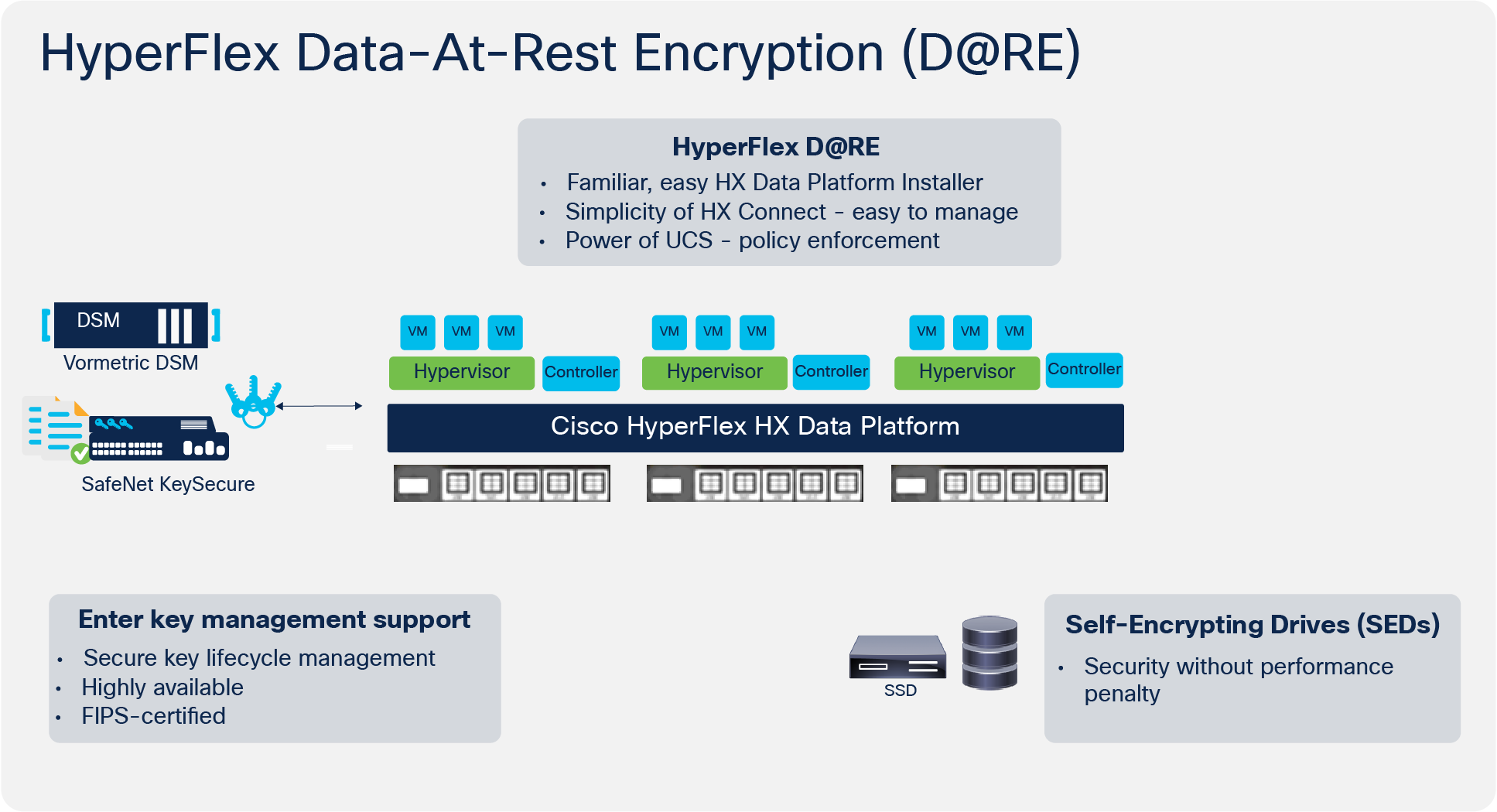
Asymmetric Encryption - Simply explainedA security key, also known as Key-Encryption Key or an authentication passphrase, is used to encrypt the media encryption key. To enable SED, you must provide a. This document discusses configuring and troubleshooting Cisco Network-Layer Encryption with IPSec and Internet Security Association and Key Management. The �master key� is what the router will use to encrypt your pre-shared keys. If you do not type this when you submit the rest of the command.